One thing I really enjoy about my job as a Technical Solutions Architect with Cisco is being able to really understand how things work. A few months ago, I was trying to create some new content for my upcoming Cisco Live session. Then a global pandemic started! The current world events presented an interesting opportunity to look a little deeper into some of the phishing campaigns we were observing across some of our security products (specifically, Cisco Email Security and Cisco Umbrella).
This blog presents some of those findings and points out how the information tied to these campaigns can be stitched together to tell a story. Our goal was to uncover how attackers create and orchestrate sophisticated campaigns to take advantage of the current pandemic. For instance, according to Umbrella researchers, over 50% of domains with “covid” or “corona” in them were malicious in early April. I find this statistic staggering!
Rise in pandemic-related phishing emails
I started looking into this issue more closely during the last week of February, while attending the RSA conference in San Francisco. I find it fascinating how quickly some of these campaigns were created and executed. Some of them are very elaborate involving compromising numerous web properties, as well as sending out legitimate-looking emails to thousands of targeted people.
Side note: I’d like to extend a huge thanks to the Cisco Talos team for helping me obtain some of this information! Working with the Talos intelligence team, we observed phishing email campaigns with topics that ranged from selling books like “Pandemic Survival – How to Survive the Corona Virus” for $37, to more juicy ads like “Military Source Exposes Shocking Truth About this Deadly Pandemic and the ‘1 Thing’ You Must Do before It’s Too Late.” Other more legitimate-looking phishing emails would supposedly redirect you to information about high-risk places in your city. I found the latter example to be the most intriguing since it didn’t have all the typos we see in many phishing emails and actually had some relevant content to offer, which made them seem more trustworthy at first glance.
Let’s take a look at one of these phishing emails below from February 26th.

A few things to note here:
- The email was spoofed to make it look like it was being sent from the Centers for Disease Control (CDC) from the account cdc-covid19@cdc[.]gov — but you couldn’t reply to that address
- Mostly accurate content, which led to a sense of trust
- Better language and grammar/punctuation usage than most phishing emails I’ve seen (again, to increase trust)
- A link that appears to point to cdc.gov but is actually pointing somewhere else (more on that later)
Of the handful of emails we examined related to the pandemic, this one stuck out as appearing more legitimate. Let’s take a closer look.
Below is a high-level visualization of what took place during this campaign.

The CDC email was especially tricky because the attackers covered their tracks. Even if you were being cautious and decided to check the email address and the URL (which appeared legitimate), you could still be a victim of an attack.
Here’s what actually happened in the course of this attack.
- The user gets the email pictured above and clicks on the “CDC” link
- Link takes them to http://healinig-yui223[.]com/[parameters]
- This site redirects the user to a compromised site hosting the Microsoft Outlook Phishing element (below are just the ones we observed with our intel)
- urbanruraldesign[.]com[.]au/[parameters]
- schooluniformtrading[.]com[.]au/[parameters]
- Users are presented with an Outlook login page with their userID pre-populated
At first you might be thinking, “How would this fool a user?”
Imagine if you are a regular user of Microsoft Outlook online. When you clicked what you thought was a link to the CDC website, you were presented with what appeared to be the Outlook login page with your username already filled in. You might simply think “Oh, in order to follow that link, I need to be logged into my email, and I’ve been logged out. So, I’ll just enter my corporate password again.”
The rest is history. If you’re like many users, you use those same credentials in other places too — across a wide range of SaaS applications, social media sites, and other websites. Of course, if you’re already following cybersecurity best practices, you won’t be re-using your passwords on multiple sites, you may use a password management solution, and probably have multi-factor authentication in place — but we don’t live in a perfect world.
To dig a little deeper into this campaign, consider the visibility that Cisco has in this space. Talos sees 400 billion emails a day and Cisco Umbrella sees over 200 billion DNS queries daily.
Taking a deeper dive…
Let’s take a look at how we studied the data to observe these patterns. Data from Cisco Umbrella Investigate shows us that the domain that people actually connected to from this email (which looked like cdc.gov but was actually healing-yui223[.]com) had a sudden spike on February 26th. Lo and behold, this was the same date as numerous instances of this phishing attack observed by Talos email intelligence.
If you visited this domain directly, you would be taken to a harmless-looking website. However, if you clicked the link in the email with the redirect parameters, you would eventually be redirected to an Outlook phishing page.
![healing-yui223[.]com DNS timeline investiation](https://cdn.umbrella.marketops.umbrella.com/wp-content/uploads/2020/04/28084954/Discovering-pandemic-themed-phishing-cyberattacks-with-threat-intelligence_Cisco-Umbrella-Blog_3-1024x679.png)
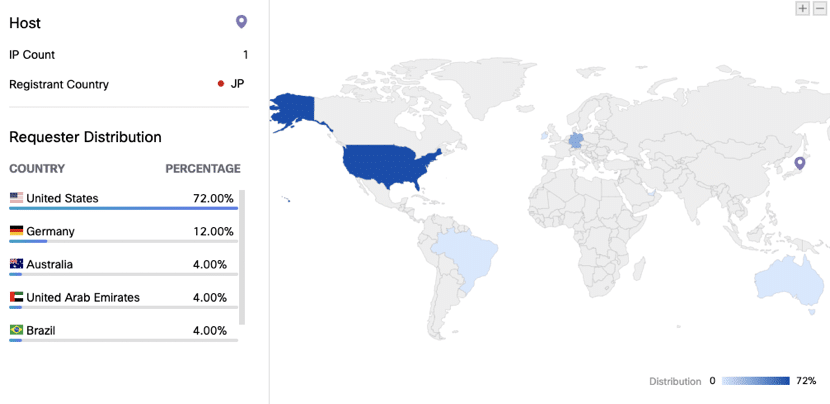
This site hardly had any traffic until a sudden spike on February 26th, which we were able to observe thanks to Umbrella Investigate. Bear in mind, this data set is just based on Umbrella’s visibility, so the real number of visits is likely much higher. We can also see the geographical distribution of requests made to this domain.
Sure enough, the requests are coming predominantly from the U.S. This shows that the cyber attackers targeted users in the U.S. which makes sense for an email claiming to be from the CDC. If people in the U.S. saw an email from the Singapore Ministry of Health (that’s another campaign I wish I had more time to go into) they likely wouldn’t take it seriously.
When the user clicks the link, they are redirected to another site which actually hosts the phishing page. Based on our analysis, the majority of traffic went to the sites shown below. Notice that they both have similar traffic patterns as the site that redirected them there.
![schooluniformtrading[.]com[.]au and urbanandruraldesign[.]com[.]au traffic analysis](https://cdn.umbrella.marketops.umbrella.com/wp-content/uploads/2020/04/28090119/Discovering-pandemic-themed-phishing-cyberattacks-with-threat-intelligence_Cisco-Umbrella-Blog_5-1024x839.png)
At some point, the URLs from these emails were passed into our sandboxing solution, Cisco Threat Grid. Threat Grid was able to perform additional analysis by playing these URLs out in a sandbox environment and assessing their threat.
Let’s look a bit further into the domain urbanruralanddesign[.]com[.]au. We can see some other URLs that were hosted on this domain. Of particular interest is the fact that the first spike appears to be related to a CDC phishing campaign, but then in early March, there is a spike related to a Wells Fargo phishing campaign. We suspect this was likely an unpatched WordPress site that was compromised and used in multiple phishing attacks.
This demonstrates the sophistication of the actors. In a matter of days, the attackers were able to orchestrate a phishing campaign that took advantage of the pandemic as a hot topic. This involves sending out thousands of legitimate-appearing targeted emails and compromising a number of web properties, all very rapidly. Only a week later, some of these compromised properties were already being used for a completely different phishing campaign.

If you’re interested in obtaining this kind of visibility and protection at the DNS layer, consider signing up for free Cisco Umbrella DNS monitoring. This service gives you fast recursive DNS service with visibility into all of your DNS queries… for free!
If you’d like to get more sophisticated threat intelligence, including data from Cisco Talos, sign up for a free trial of Cisco Umbrella, and get content and security blocking, along with much more. Also, you can extend the initial Cisco Umbrella 14-day trial period to 90 days by contacting the Cisco sales team. This offer will be available from now until July 1, 2020.
I hope you found this blog post helpful. If you’re interested in learning more about phishing attacks and threat intelligence, I’ll be hosting a session at the virtual Cisco Live event. Sign up for my session there or catch me on Twitter @rivimont.
