Welcome to the first monthly edition of the Cisco Umbrella Threat Spotlight, which is produced by our cybersecurity threat analysis team. This team supports the collection, analysis and distribution of threat intelligence from the Cisco global cloud architecture.
The Cisco Umbrella security researchers take mathematical concepts and find new ways to apply them to security data — helping us uncover threats before attacks even launch. They leverage advanced data mining techniques, machine learning and behavioral models, coupled with security domain expertise to identify threats and protect our customers.
We hope this threat research will be helpful to Umbrella customers in identifying and stopping cybersecurity threats as they arise.
This month, we’re examining a remote access trojan (RAT), another trojan that frequently works with the RAT, and an information stealer. While each possesses unique features and characteristics, they are good examples of the ongoing trend toward complex, multi-staged cyber attacks.
Threat Name: LodaRAT
Threat Type: RAT (Remote Access Trojan)
Actor: LodaRAT – Kasablanka Group
Delivery and Exfiltration:
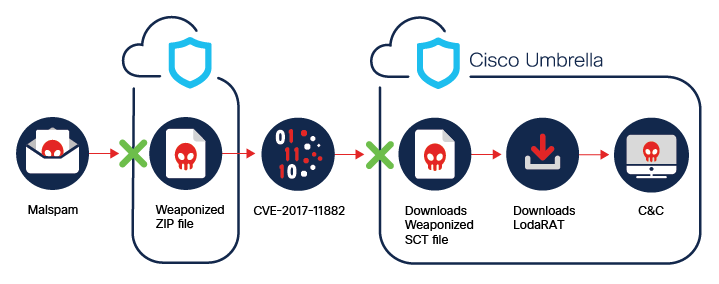
Description: Loda is a remote access trojan (RAT) for Windows and Android systems. Loda campaigns use malspam and websites hosting malicious documents to begin a multi-stage infection chain, which ultimately serves a malicious file to install LodaRAT on targeted systems. While the main purpose of this RAT is to steal usernames, passwords, and cookies saved within browsers, it also has keylogging, sound recording, and screenshot abilities.
LodaRAT Spotlight: In the latest campaign, the malicious document exploits CVE-2017-11882 to download and run the SCT file. Once the exploit is triggered, an SCT file initiates download of the LodaRAT binary. Apart from data stealing abilities the malware contains a command- and script-running capability, which provides the malware flexibility to perform a wide range of tasks. Another notable new command is “Sound|” which uses the BASS audio library to capture audio from a connected microphone. The C2 hostname and port are both hardcoded in the sample in plain text. This new campaign targets Bangladeshi users of Windows and Android systems. The fact that the threat group has moved into hybrid campaigns targeting Windows and Android shows a group that is thriving and evolving. Giving that there are indications that the group using LodaRAT is looking for direct financial gain (there is no related ransomware or banking activity), organizations and individuals should be aware of this threat group.
Target geolocations: US, Costa Rica, Brazil, Argentina, India
Target data: Credentials, Cookies from browsers, Stored information
Target businesses: Any
Exploits: CVE-2017-11882
Mitre Att&ck, LodaRAT:
Initial access: Spearphishing Attachment
Persistence: Registry Run Keys / Startup Folder, Scheduled Task
Evasion: File and Directory Permissions Modification, Obfuscated Files or Information
Collection: Audio Capture, Automated Collection, Clipboard Data, Screen Capture, Video Capture
Exfiltration: Data Obfuscation, Exfiltration over Web Service
References: Talos blog – LodaRAT
IOCs:
Domains:
info.v-pn[.]co
lap-top[.]xyz
av24[.]co
bdpolice[.]co
isiamibankbd[.]com
bangladesh-bank[.]com
zep0de[.]com
bracbank[.]info
IPs:
160.178.220[.]194
194.5.98[.]55
107.172.30[.]213
For additional information: Talos blog – LodaRAT
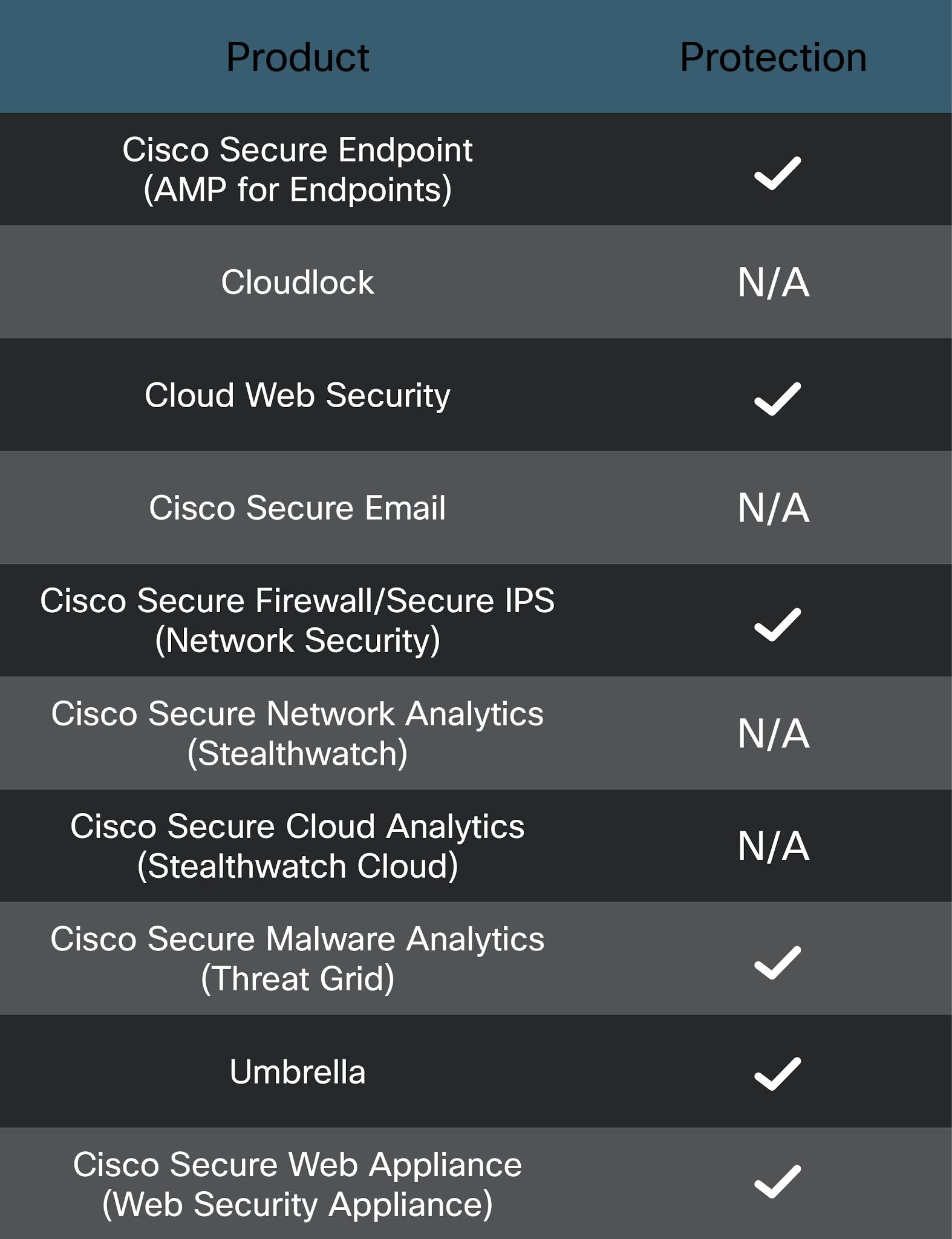
How to stop LodaRAT: Cisco Umbrella can detect and block a LodaRAT cyber attack. A checklist of Cisco products that can detect and block this cybersecurity threat is below.
Threat Name: Agent Tesla
Threat Type: Trojan
Actor: Agent Tesla – Raticate
Delivery and Exfiltration:
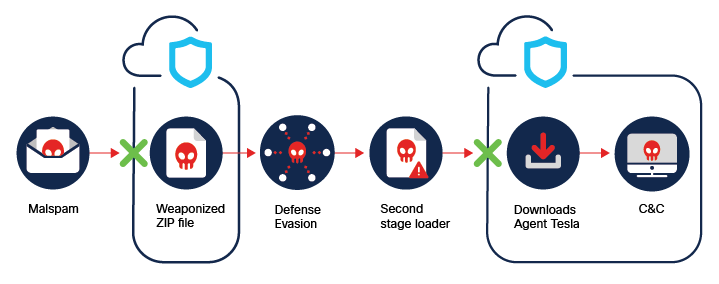
Description: Trojan first observed in 2014, Agent Tesla is marked by a strong support presence from its developers. It was distributed by GuLoader through phishing attachments posing as information about the COVID-19 outbreak. A variety of attackers use the malware to steal user credentials and other information from victims through screenshots, keyboard logging, and clipboard capture. Because the malware’s compiler hard-codes operator-specific variables at build time, Agent Tesla behavior can vary widely—and the malware continues to evolve.
Agent Tesla Spotlight: In the latest campaign, Agent Tesla was delivered as malicious attachments in emails. The malware uses a number of methods to defeat sandbox and static analysis and evade endpoint detection. These methods include the use of packers to obfuscate code, and the use of components hosted legitimate websites. The infection process consists of several stages, where malware attempts to overwrite code in Microsoft’s AMSI, and uses Hastebin to download an obfuscated loader which installs the final payload. New versions of Agent Tesla can use HTTP, SMTP, FTP, and Telegram chat protocol for communication. When installed the RAT archives persistence, fingerprints infected machines and steals credentials. Other capabilities include screenshot exfiltration and keystroke capture.
Type: Trojan
Target geolocations: Any
Target data: Credentials, Browser Cookies, System Fingerprints
Target businesses: Any
Mitre Att&ck, Agent Tesla:
Initial access: Spearphishing Attachment
Persistence: Registry Run Keys / Startup Folder
Evasion: Impair Defenses: Disable or Modify Tools, Virtualization/Sandbox Evasion: System Checks, Virtualization/Sandbox Evasion: Time Based Evasion
Collection: Automated Collection, Clipboard Data, Screen Capture
Exfiltration: Exfiltration over Web Service
References: Agent Tesla
IOCs:
Domains:
3ptechnik[.]xyz
89gospel[.]com
arles-cz[.]co
delcoronascardigli[.]xyz
itrader-germany[.]de
orator[.]net
p0lybrands[.]com
proxyfreaks[.]com
qxq.ddns[.]net
sciencepub123[.]com
aruscomext[.]com
chemweb[.]xyz
cleannharbor[.]com
crmsynergies[.]xyz
cumjtas[.]com
energstylgroup[.]com
protecclab[.]com
scrablex[.]com
top-semi[.]xyz
perfumela[.]com
How to stop Agent Tesla: Cisco Umbrella can detect and block an Agent Tesla cyber attack. A checklist of Cisco products that can detect and block this cybersecurity threat is below.

Threat Name: Masslogger
Threat Type: Information Stealer
Actor: MassLogger
Delivery and Exfiltration:

Description: MassLogger is an Information Stealer. It is mainly distributed by delivery mechanisms which download encrypted payloads such as GuLoader. The C2 carrier protocol depends on the sample’s configuration, but it can send the results over SMTP and/or FTP to its control server. The creator of MassLogger, known as NYANxCAT, is responsible for several other well-known and prolific RATs, including LimeRAT, AsyncRAT, and other RAT variants. MassLogger is being improved consistently over time. Updates add new targets for its credential stealing functionality and include measures taken that would reduce automated detection. Other functions include searching for files with a specific file extension and exfiltrating them.
MassLogger Spotlight: Although operations of the Masslogger trojan have been previously documented, Cisco Talos found the new campaign notable for using the compiled HTML file format to start the infection chain. This file format is typically used for Windows Help files, but it can also contain active script components, in this case JavaScript, which launches the malware’s processes. In case of commodity spyware such as Masslogger, it is the infection chain and contextual information that distinguish the individual actors behind each campaign. This infection chain seems to focus on business users, with email being the infection vector. The email contains a RAR attachment with a compiled HTML (.chm) attachment. The rest of the chain is split between JavaScript, PowerShell and .NET. The email is written in the language of the targeted recipient’s top-level domain. The attachment file name for the latest campaign is chosen according to the email subject, with possible random strings prepended. When the user opens the attachment with the default application the chain of exploitation is launched. It results in MassLogger malware being installed on the workstation. This version of Masslogger contains the functionality to target and retrieve credentials from the following applications:
- Pidgin messenger client
- FileZilla FTP client
- Discord
- NordVPN
- Outlook
- FoxMail
- Thunderbird
- FireFox
- QQ Browser
- Chromium based browsers (Chrome, Chromium, Edge, Opera, Brave)
Stolen data can be exfiltrated through SMTP, FTP or HTTP protocols. In this case, the exfiltration was conducted over FTP.
Target geolocations: Turkey, Latvia, Italy, Bulgaria, Lithuania, Hungary, Estonia, Romania, Spain
Target data: Credentials from Web Browsers, Local Data
Target businesses: Any
Exploits: N/A
Mitre Att&ck, MassLogger:
Initial access: Spearphishing Attachment
Persistence: Registry Run Keys / Startup Folder
Evasion: Deobfuscate/Decode Files or Information, Virtualization/Sandbox Evasion
Execution: Command and Scripting Interpreter: JavaScript/JScript
Collection: Clipboard Data, Input Capture
Discovery: System Information Discovery, Software Discovery
Credential Access: Credentials from Password Stores: Credentials from Web Browsers, Input Capture: Keylogging
Exfiltration: Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted/Obfuscated Non-C2 Protocol
References: Talos Blog – MassLogger
IOCs:
Domains:
sinetcol[.]co
becasmedikal[.]com[.]tr
risu[.]fi
topometria.com[.]cy
bouinteriorismo[.]com
optovision[.]gr
hotelaretes[.]gr
jetfleet24[.]com
med-star[.]gr
For additional information: Talos blog – MassLogger
How to stop MassLogger: Cisco Umbrella can detect and block a MassLogger cyber attack. A checklist of Cisco products that can detect and block this cybersecurity threat is below.

