This has been a busy month for cyber attackers, and the Cisco Umbrella team – in conjunction with Cisco Talos – has observed several new threats for users to be aware of.
In this month’s edition of the Cybersecurity Threat Spotlight, we discuss a wiper making its way through Ukraine, a dropper targeting India and China, and a newly discovered Trojan targeting EU banks.
Want to see Cisco Umbrella in action? Sign up for a free trial today!
HermeticWiper
Threat Type: Wiper
Attack Chain:

Description: HermeticWiper is a data destructing malware observed in attacks targeting Ukraine. This wiper comes as a small executable with a valid digital signature issued to “Hermetica Digital Ltd.” The malware leverages embedded resources to interact with storage devices present on infected systems. The applicable embedded driver is extracted, loaded into the wiper’s process memory space, decompressed, and written to the disk before the wipe process. The wiper disables the generation of crash dumps and corrupts the first 512 bytes to destroy the MBR of physical drives. For partitions, it disables the Volume Shadow Copy Service and uses different destructive mechanisms on the partitions depending on whether they’re FAT type or NTFS type. The wiper also attempts to corrupt housekeeping files. During the final stage, HermeticWiper waits for all sleeping threads to complete and initiates a reboot to ensure the success of the wiping activity.
HermeticWiper Spotlight: Cisco Talos has become aware of a series of wiper attacks going on inside Ukraine. One of the wipers used in these attacks has been dubbed “HermeticWiper.” Deployment of this destructive malware began on February 23, 2022. The malware has two components designed for destruction: one targeting the Master Boot Record (MBR) and another targeting partitions.
Target Geolocations: Ukraine
Target Data: Physical Drivers, Partitions
Target Businesses: Government Sector
Exploits: N/A
Mitre ATT&CK for HermeticWiper
Initial Access:
Valid Accounts
Discovery:
System Information Discovery
File and Directory Discovery
Persistence:
Create or Modify System Process: Windows Service
Execution:
Native API
Evasion:
Modify Registry
Impact:
Disk Wipe: Disk Structure Wipe
Inhibit System Recovery
Service Stop
System Shutdown/Reboot
Privilege Escalation:
Access Token Manipulation
IOCs1
Hashes:
0385eeab00e946a302b24a91dea4187c1210597b8e17cd9e2230450f5ece21da
1bc44eef75779e3ca1eefb8ff5a64807dbc942b1e4a2672d77b9f6928d292591
2c10b2ec0b995b88c27d141d6f7b14d6b8177c52818687e4ff8e6ecf53adf5bf
3c557727953a8f6b4788984464fb77741b821991acbf5e746aebdd02615b1767
Additional Information
Threat Advisory: Hermetic Wiper
Which Cisco Secure Products Can Block
Cisco Secure Endpoint
Cisco Secure Email
Cisco Secure Firewall/Secure IPS
Cisco Secure Malware Analytics
Cisco Umbrella
SDUser
Threat Type: Dropper
Attack Chain:
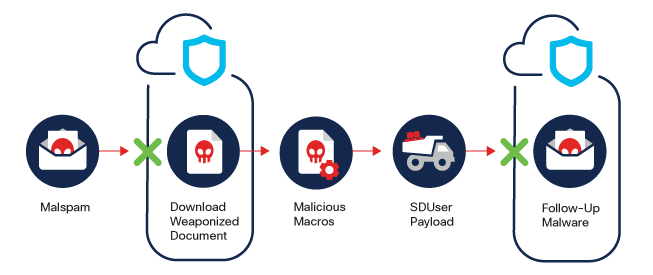
Description: SDUser is a VBA-based dropper that is used by Advanced Persistent Threat (APT) groups. The functionality of the payload includes command and control protocol, anti-sandboxing techniques, and a reverse shell mechanism.
SDUser Spotlight: In June 2021, Cisco Talos researchers discovered a malicious Excel spreadsheet that attempted to drop a previously unknown RAT. A month later, they discovered another closely related spreadsheet. These samples were internally referred to as “SDUser” sampled due to the specific PDB string left in the binary payload.
More recent analysis shows similar code being used by two different APT groups: Transparent Tribe, which targets organizations in India, and Donut, which targets organizations in Pakistan and China. These two different threat actors may use code from the same source in their attacks, which means that their attacks would display similarities despite being conducted by different groups. Code reuse, adopting techniques from successful attacks, and deliberate integration of evidence designed to fool analysts can disguise the true perpetrator and lead to these attacks being attributed to different groups.
Target Geolocations: Pakistan, China
Target Data: User Credentials, Browser Data, Sensitive Information
Target Businesses: Any
Exploits: N/A
Mitre ATT&CK for SDUser
Initial Access:
Phishing: Spearphishing Attachment
Discovery:
Peripheral Device Discovery
Query Registry
Execution:
Command and Scripting Interpreter
Evasion:
Obfuscated Files or Information
Virtualization/Sandbox Evasion: System Checks
Command and Control:
Application Layer Protocol
Web Service
IOCs1
Domains:
microsoft-updates[.]servehttp[.]com
microsoft-patches[.]servehttp[.]com
microsoft-docs[.]myftp[.]org
IPs:
45.153.240[.]66
46.30.188[.]222
Additional Information:
What’s with the shared VBA code between Transparent Tribe and other threat actors?
Which Cisco Secure Products Can Block:
Cisco Secure Endpoint
Cisco Secure Email
Cisco Secure Firewall/Secure IPS
Cisco Secure Malware Analytics
Cisco Umbrella
Cisco Secure Web Appliance
Xenomorph
Threat Type: Mobile Trojan
Attack Chain:

Description: Xenomorph is an Android Banking Trojan. It is capable of stealing credentials via overlay attack, and it uses SMS and notification interception to log and use potential 2FA tokens. Stolen data is sent to the C2 for further exploitation.
Xenomorph Spotlight: Xenomorph was initially discovered in February 2022. It is distributed through the official Google Play Store. It targets users of 56 different European banks and cryptocurrency wallets. Capabilities include – but are not limited to – stealing credentials, SMS and notification interception, excessive logging, and data exfiltration. The core engine is designed as a modular system and still appears to be in the development stage. Malware heavily relies on the overlay attack mechanism to steal personally identifiable information (PII) and other sensitive data. Collected data is exfiltrated to an attacker-controlled server using the open-source project RetroFit2.
Target Geolocations: EU
Target Data: User Credentials, Browser Data, Sensitive Information
Target Businesses: Any
Exploits: N/A
Mitre ATT&CK for Xenomorph
Initial Access:
Deliver Malicious App via Authorized App Store
Execution:
Native Code
Evasion:
Masquerading as Legitimate Application
Credential Access:
Capture SMS Messages
Input Capture
Command and Control:
Standard Application Layer Protocol
Exfiltration:
Data Encryption
Standard Application Layer Protocol
IOCs1
Domains:
simpleyo5[.]tk
simpleyo5[.]cf
art12sec[.]ga
kart12sec[.]gq
homeandofficedeal[.]com
Additional Information:
Xenomorph: A newly hatched Banking Trojan
Which Cisco Secure Products Can Block
Cisco Secure Firewall/Secure IPS
Cisco Secure Malware Analytics
Cisco Umbrella
Cisco Secure Web Appliance
1 Additional IOCs can be found in the associated Talos Blog articles
