84.7% of cyberattacks involve phishing. In such a scenario, it becomes very important to understand the various ways a phishing attack could occur. Phishing URLs are commonly found on cloud providers. This article will take you through why cloud providers are being used increasingly for phishing campaigns and what pattern an attack on these sites usually follows.
Phishing pages hosted on cloud services like Microsoft Azure can trick users into believing that they are visiting a legitimate site.
Firstly, these pages have the green lock sign displayed on the site. Users who don’t really go into the details may see the green lock symbol and think that the site is safe. However, the green lock merely symbolizes that the site is secure, which means that the traffic is encrypted, and the site itself may not necessarily be safe.
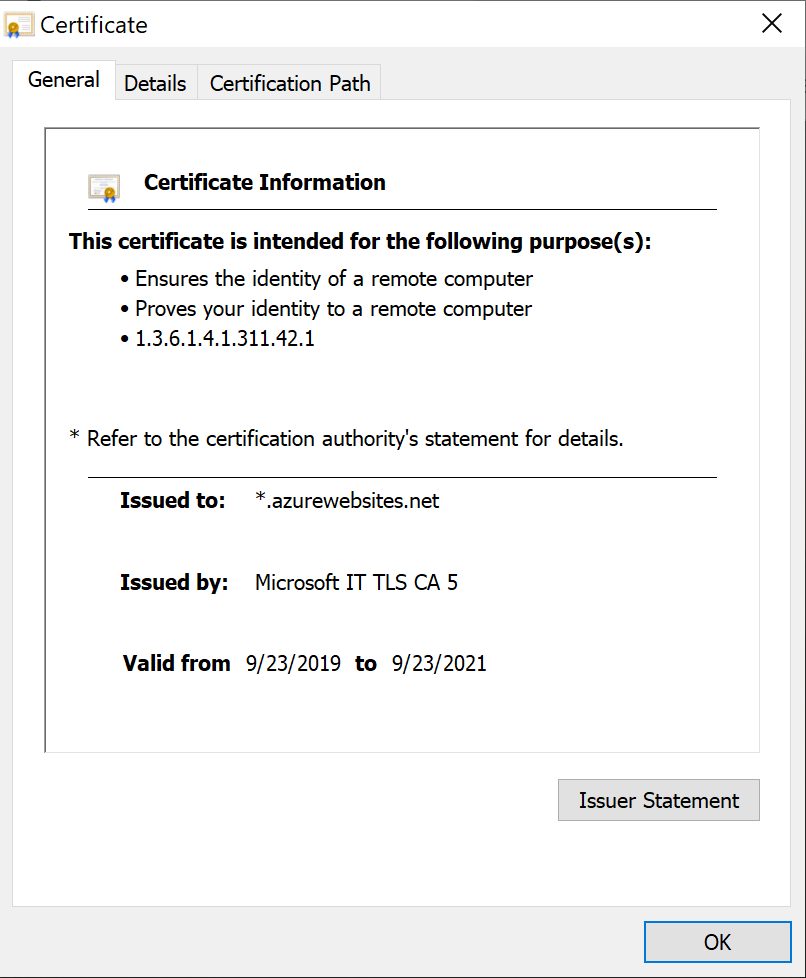
Even if a user knows this difference and decides to inspect further, the page will have a valid SSL certificate signed by Microsoft. This happens because the page is hosted on Microsoft Azure.
Moreover, many times the URL may contain windows[.]net or azurewebsites[.]net which may lead users to believe that it is a legitimate Microsoft site.
Every week we identify many phishing sites that behave in this way.
Let’s take a look at one of them:
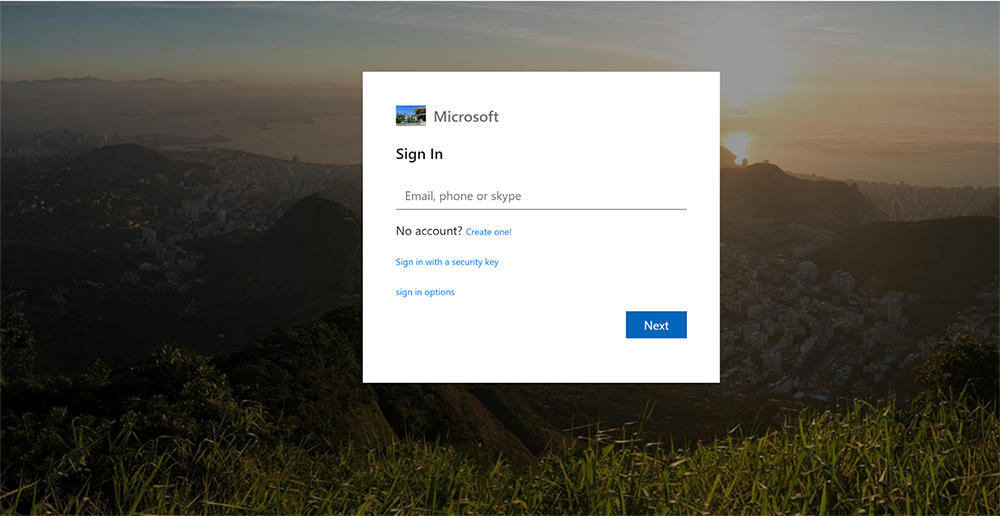
hXXps://enq42yzh.azurewebsites.net/caiTxU/ when a user goes to this url, it shows a Microsoft login page.
The domain is registered to Microsoft, as per the WHOIS information available.

The SSL certificate of the site is issued by Microsoft, which again leads the user to think the site is a legitimate one.
However, when a user enters the login credentials on this page, the attacker gets the login ID and password, thus making the phishing attempt successful.
To see how this happens, we inspect the source code of the page. In this particular case, after the user enters login credentials and clicks on the ‘Login’ button, they are simply taken back to the login page again. The attacker gets the user credentials.
This can be seen in the source code of the page:

In other cases, the source code may contain heavily obfuscated text. In the example below, the snippet contains text that is likely base64 encoded.

Here, we took one such encoded part and decoded it. The decoded JavaScript code is shown below:

Upon analyzing the code, we can see a variable gate that is a URL: hXXps://voicecenterserved[.]azurewebsites.net/assets/gate.php.
A POST request is made to this URL through which the email and password entered by the user is sent. This destination URL is likely where the attacker stores the credentials. It acts as a C&C server. Sometimes, the link to the C&C server can be encoded in a hex string or is available directly in the page source of the site.


The credentials obtained may then be used for a number of different things. These can be used to access various accounts of the victim, sell them to various third parties, use them for a particular campaign, etc.
Phishing attacks of this type have been on the rise over the last few years. Phishing attacks targeted at SaaS and other webmail services still continue to be the biggest category of phishing (as per APWGs Q1 2020 report). By getting a user’s Microsoft or other similar SaaS login credentials, the attacker gets access to multiple accounts linked to that particular user ID. This makes the user vulnerable to a very wide threat landscape.
Conclusion
Cisco Umbrella resolves over 220 billion DNS requests daily, giving our researchers a unique view of the Internet to better identify trends on threats, faster. We are constantly finding new ways to uncover “fingerprints” that attackers leave behind and ways to build new statistical and machine learning models to automatically identify attacker infrastructure to pre-emptively neutralize it. This way, attacks can be stopped even before the specific nature of the attack is fully identified.