Spend enough time in cybersecurity and you’re bound to have heard colleagues, analysts, and consultants suggest adding DNS-layer protection to your security stack. It’s easy to understand the appeal – using the internet’s infrastructure to block connections to malicious or unwanted domains can help protect any network from online hazards. But recently, with the conversation shifting from single-point solutions to the integrated networking and security services of Gartner’s SASE model, you may find yourself wondering where a secure DNS solution fits in.
Hailed as the future of cybersecurity and network connectivity – a Jetsons-esque model that can revolutionize stone-age infrastructure – Gartner’s SASE framework converges traditional siloed networking and cybersecurity solutions into a single, cloud-delivered service. The approach streamlines operations, enhancing functionality by making it easy to deploy and manage both networking and security systems. While not necessary to a basic SASE solution, integrated DNS-layer security can enhance the security elements of your SASE solution by blocking threats before they reach your network or endpoints.
If your organization is like most, Gartner’s SASE model may be more aspirational than ready to implement. After all, most enterprises boast an architecture characterized by fragmented, siloed solutions and overlapping technologies that are difficult to manage. That’s why many security teams choose to implement SASE in stages, starting by updating their security infrastructure. And there’s no better place to begin that process than at the DNS layer. When you partner with the right provider, securing your DNS resolvers can be accomplished in as little as 30 minutes and provide cloud-based security without latency while you update the rest of your security stack.
In our eBook A Roadmap to SASE: Navigating the challenges of network security beyond the data center, we discuss how an organization can implement a cybersecurity stack that fits into Gartner’s SASE architecture. But if you’d like to learn more about how to begin your journey with DNS-layer security, this article is for you.
Why should you implement security at the DNS-layer?
Often referred to as the foundation of the internet, the domain name system (DNS) serves as the bedrock for internet connectivity. Every time you type a domain name into an internet browser or open up an internet-enabled application, recursive and authoritative DNS servers retrieve the associated internet protocol (IP) addresses. This allows your device to connect to the servers hosting the domain you want to access.
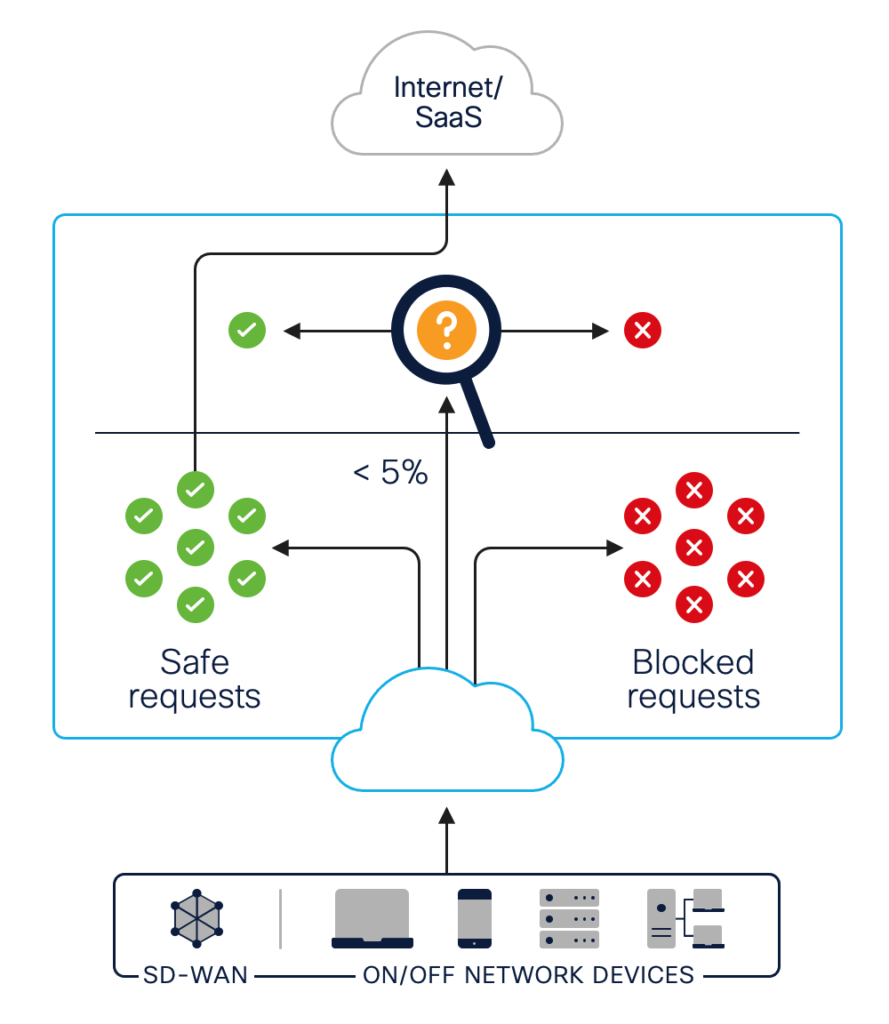
Despite the fact that DNS plays an integral role in internet infrastructure, most organizations do precious little to secure the DNS layer from threats. In fact, unless you have DNS-layer security, odds are the DNS packets typically used to communicate IP addresses won’t even be inspected as they move through your network. What’s more, most cybersecurity solutions don’t even register anomalous DNS activity – like DNS tunneling – that can indicate an in-progress attack.
As you can imagine, this makes the DNS layer the perfect avenue for bad actors to use when infiltrating networks. In many of today’s more sophisticated ransomware attacks, for example, bad actors will use DNS packets to upload malware to a device. Then, they’ll establish DNS tunnels between their servers and their victims’ devices. This connection between attacker and victim allows for the exfiltration of sensitive data and the execution of command and control operations. These kinds of attacks can cripple an entire network within hours, and most SecOps teams won’t even notice the anomalous DNS-layer activity until it’s too late.
How does DNS-layer security work?
When you partner with a recursive DNS-layer security provider, all DNS activity occurring in your network will be facilitated by proprietary recursive DNS servers (also known as resolvers) that the vendor operates. Your secure DNS provider will configure these resolvers to protect against threats to your network by:
- Identifying risky or dangerous domains and preventing your users from connecting to them
- Preventing users from connecting to non-sanctioned domains where the risk of data loss is higher
- Identifying anomalous DNS-layer activity on a network that can indicate an in-progress attack
Whether your SecOps team is using DNS-layer security to block attacks before they can begin or mitigate attacks before they can cause widespread damage, it’s easy to see the value of this security solution. But when you partner with a SASE provider to secure DNS activity in your network, the benefits increase exponentially.
How do these solutions fit into a SASE security stack?
Remember, the point of Gartner’s SASE model is to streamline both networking and security operations by converging them into a single, comprehensive service. With goal as a guiding principle, it’s easy to understand why DNS-layer security – which serves as an easy-to-implement, easy-to-manage first line of defense against threats – plays an important role in enhancing the security elements of a SASE solution.
When backed by a robust threat detection network – a critical part of security infrastructure in a SASE solution – secure DNS resolvers can identify the risky domains that threat actors use to host malware. These DNS resolvers can be easily configured to block user connections to these domains. Preventing attacks before they even begin lessens the strain on other parts of a security stack, reducing the number of alerts a SecOps team has to deal with and streamlining security operations on the whole.
Choosing secure DNS you can integrate into a SASE solution
As we mentioned earlier, you may not be ready to upgrade your networking and security infrastructure to fully align with Gartner’s SASE model. But investing in a secure DNS solution can be the perfect way to start your journey towards SASE, enhancing your security posture in the present while laying the groundwork for a more comprehensive and integrated system in the future.
When investing in DNS-layer security as a stepping-stone to SASE, keep these principles in mind:
Partner with a SASE vendor that offers a product that secures the DNS layer
One of the key principles of Gartner’s SASE model is integration, whether that’s an integrated security stack that can be managed from a single interface or integrated security and networking solutions designed to operate seamlessly together. This is why it makes sense to purchase DNS-layer security from a SASE vendor. These vendors will work with you to upgrade your security stack and network architecture over time, ensuring you won’t need to switch vendors or solutions down the line. These vendors also know how to best deploy DNS-layer security in the present so that you can enjoy some degree of cloud-native protection for the duration of your SASE journey.
Find a DNS-layer security solution that integrates extra functionality
SASE vendors design converged security solutions. So, if you’re getting secure DNS services from a SASE vendor, they may have already integrated some of that converged functionality into the DNS protection package you’re purchasing.
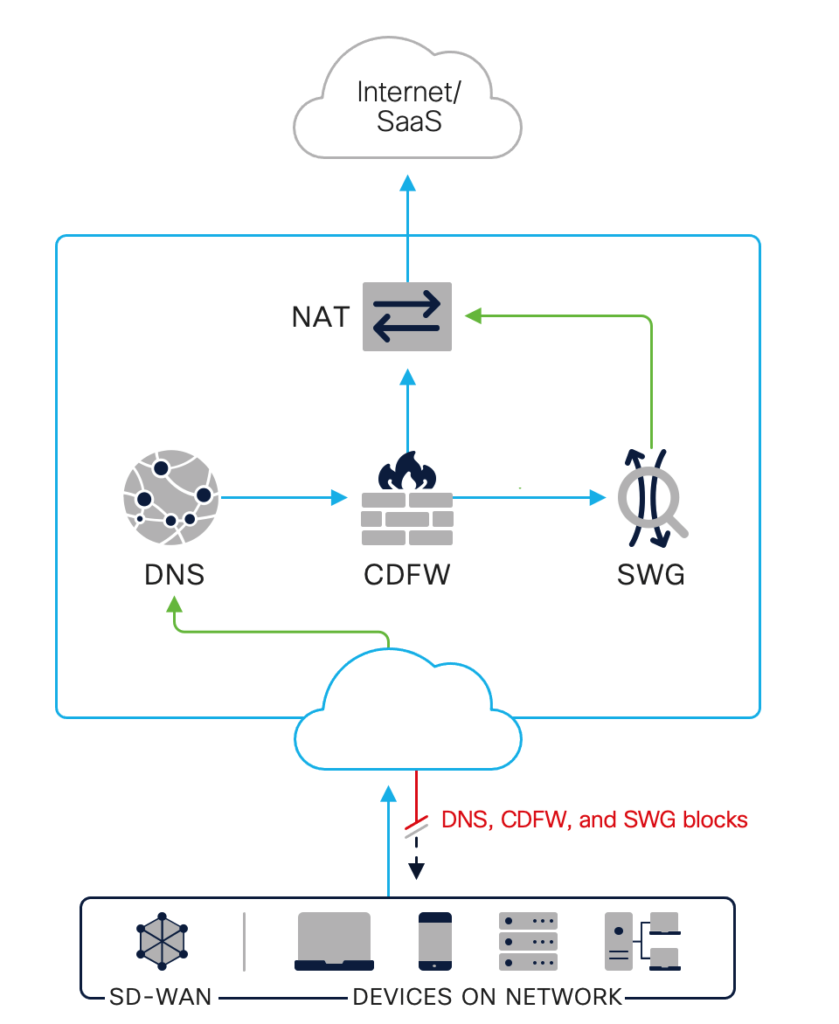
For example, the Cisco Umbrella DNS Advantage package also allows users to enjoy limited secure web gateway (SWG) and cloud access security broker (CASB) functionality. Security teams can proxy web traffic associated with risky domains or perform app discovery and control activities – enhanced security functionality typically associated with SWG or CASB. Unlike appliances, our cloud-native service protects devices both on and off the corporate network. And unlike agents, the DNS-layer protection extends to every device connected to the network – even IoT. Cisco Umbrella really can be deployed everywhere, since the majority of internet-connected devices use recursive DNS services.
It’s time to start your journey to SASE with secure DNS
Your journey towards Gartner’s SASE model may take time, but investing in a forward-thinking DNS-layer security solution can also allow you to enjoy immediate results. After all, what other solution can quickly, easily, and cost-effectively improve an organization’s security posture for both on-premises and remote workers?
Download our eBook A Roadmap to SASE: Navigating the challenges of network security beyond the data center today to start plotting out your SASE journey. Or, sign up for our Cisco Umbrella free trial to learn how implementing a solution that secures the DNS layer can benefit your organization in the present with easy-to-use controls and effortless integration.