It’s hardly a stretch to say that the COVID-19 pandemic has pushed most of the world online. The Internet has become an integral part of our daily lives – how we engage with each other, attend classes, do business. In this brave new Internet-enabled world, security solutions like remote browser isolation have become more important than ever. After all, bad actors know the importance of the world wide web and are more than willing to exploit our dependence on it.
For companies with remote employees – all of whom require consistent interaction with the Internet – remote browser isolation (RBI) offers a way to protect their increased attack surface without the need to install any agents or browser plug-ins on the endpoint. Malicious javascript, malvertising (malicious ads injected in web pages via exploits or compromised ad networks), exploit kits, drive-by downloads and many other attacks target users interacting with web content via their browser. Since this is the main way the average user engages with online content, finding an RBI solution that integrates into your security stack and offers robust coverage is critical.
How Secure Is Your Average Browser?
The short answer: Not really. HIGH severity vulnerabilities in browsers are patched quite often. For example, Google recently issued multiple patches for 14 browser vulnerabilities. For Patch Tuesday, Microsoft has issued patches for six vulnerabilities targeting the Windows Environment. While the browser zero days are primarily affecting Chrome/IE browsers, since Microsoft Edge is also now based on Chrome, Edge users will also be vulnerable to these flaws. Some of them, for example CVE-2021-33742 (Windows MSHTML Platform Remote Code Execution) and CVE-2021-30551 (Type Confusion in V8), are being exploited in the wild. Once a browser with such a vulnerability is connected to a malicious site, it gives cybercriminals an opportunity to not just compromise the user’s machine but the whole network as well.
Organizations have to use a layered approach to try to mitigate this risk. It can be done by utilizing DNS protection to block known malicious websites, Newly Seen domains (category offered by Cisco Umbrella), different categories of the domains implemented through Content Policies. However, this approach might not be enough when a highly reputable domain gets compromised. At the same time, some organizations have to lower strictness of web security policies during the pandemic and mandatory work from home times. So how can companies provide their employees with internet access that doesn’t impact their ability to perform work while still protecting the organization?
Remote Browser Isolation Meets the Needs of Modern Cybersecurity Teams
In 2017, Amy Ann Forni and Rob van der Meulen of Gartner made the case for RBI solutions, stating:
Almost all successful attacks originate from the public internet, and browser-based attacks are the leading source of attacks on users. Information security architects can’t stop attacks, but can contain damage by isolating end-user internet browsing sessions from enterprise endpoints and networks. By isolating the browsing function, malware is kept off of the end-user’s system and the enterprise has significantly reduced the surface area for attack by shifting the risk of attack to the server sessions, which can be reset to a known good state on every new browsing session, tab opened or URL accessed.1
That’s why Cisco Umbrella has moved to provide users with this kind of protection, offering remote browser isolation as an add-on to SIG Essentials and SIG Advantage packages.
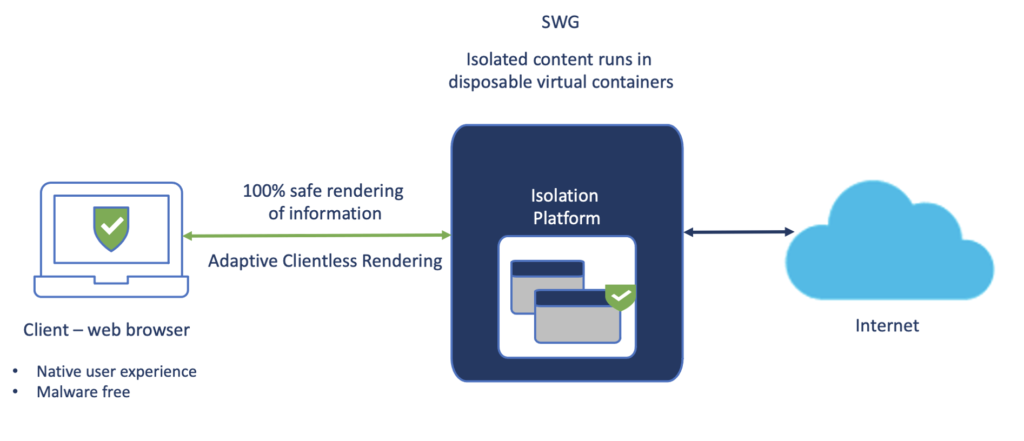
RBI protects users from potential malware and other threats by redirecting browsing to a cloud-based host. Isolation is achieved by serving up the web content to users via a remotely spun up surrogate browser located in the cloud. Typically, when a user’s browser is compromised, the attacker achieves access to the machine the browser runs on. However, with RBI, the remote browser runs in an isolated container in the cloud, thus mitigating the attack surface. The content from the remote browser is rendered in the user’s local browser without impacting the end user experience.
Sourcing Remote Browser Isolation Through Cisco Umbrella
Remote Browser Isolation (RBI) for Cisco Umbrella is available as three exclusive add-ons, all with varying degrees of isolation options:
Isolate Risky
Security Categories:
- Malware
- Command and Control Callbacks
- Phishing Attacks
- Potentially Harmful
Content Categories:
- Uncategorized
Isolate Web Apps
Content Categories:
- Chat
- File Storage
- File Transfer Services
- Instant Messaging
- Organized Email Professional Networking
- Social Networking
- Webmail
Applications:
- Cloud Storage (eg. Box, Dropbox, Google Drive)
- Collaboration (eg. Slack, WhatsApp, Facebook Messenger)
- Office Productivity (eg. Smartsheet, Lucidchard, Gmail)
- Social Media (eg. Facebook, Twitter, Instagram)
Isolate Any
Any security categories, content categories, applications, and destination lists can be isolated.
In the recording below, we demonstrate how easy it is to enable the remote browser isolation feature for an added layer of protection. We also show the functionality of RBI and how it protects even vulnerable browsers from dangerous exploits including zero-days attacks aimed at browsers.
1 Gartner, Gartner Identifies the Top Technologies for Security in 2017. Amy Ann Forni, Rob van der Meulen 2017.
