It’s no secret that security professionals today face mounting challenges trying to keep up with sophisticated attackers. Whether it’s responding to a single, isolated incident, or researching a long-running, complex threat scenario, security teams require historical data from within and outside of their organizations in order to properly triage and provide data points to justify their actions.
When it comes to evaluating domains, security analysts need more history about a domain: DNS record changes, yes, but also the evolution of goodness or badness of the domain over time. For example, consider two domains that are very similar to each other – hosted in the same IP space, with similar unique requesting clients and request patterns. Both are benign today but one has skeletons in its closet; it has a history of being tagged with security events such as malware. As a security specialist responsible for securing your organization, you’d be more interested in this second domain, no? And of course you would not want to miss out on this rich historical data as you triage.
Another frustrating challenge for security analysts is dealing with retroactive investigations. Indicators of Compromise (IOCs) can be published long after an actual compromise took place. Often attackers will wait until the time is right to utilize infrastructure they’ve prepared for an attack, sometimes keeping domains dormant for years. You want to be able to inspect suspicious domains and IPs but you certainly do not want to tip off or alert bad actors that they are under suspicion. This could cause them to evade you by ditching the infrastructure they had been standing up.
So how can we help your SOC respond faster to threats?
We believe security systems should empower your people to investigate and respond to threats faster. Cisco Umbrella Investigate gives analysts real-time access to all of our threat intelligence about domains, IPs and malware across the internet. Security analysts love Investigate because it enables them to:
- Better prioritize incident investigations
- Speed up incident investigations and response
- Easily integrate Investigate data other security orchestration tools
Investigate is available via a web console or an API.
Introducing enhanced Passive DNS
For years, we’ve provided teams with DNS-based security products to enhance their existing security stacks. We are delighted to announce our new and improved Passive DNS (pDNS) capability. Rich pDNS context helps Incident Responders investigate observables by providing a quick summary of past key events and security categorizations for domains and IPs. Our pDNS intelligence empowers Threat Hunters to get better visibility into critical historical events and relationships resulting in faster triage and more effective investigations.
There are several factors that make Cisco Umbrella Investigate’s Passive DNS feature unique. First, it’s the massive volume of our pDNS database – it is the largest in the world. Umbrella resolvers analyze over 180 billion DNS requests daily. This unique view of the internet enables researchers to better identify trends on threats, faster.
In addition, we do not just share traditional pDNS (DNS record change snapshots over time), we go beyond that and also display the security categorization data over time. This is useful for identifying not only which domains are categorized as malicious today but also for gaining a more comprehensive understanding of a domain’s history. For example, a domain could be benign one day, compromised, and some time later, remediated. Without, pDNS you would not be able to get this full context.
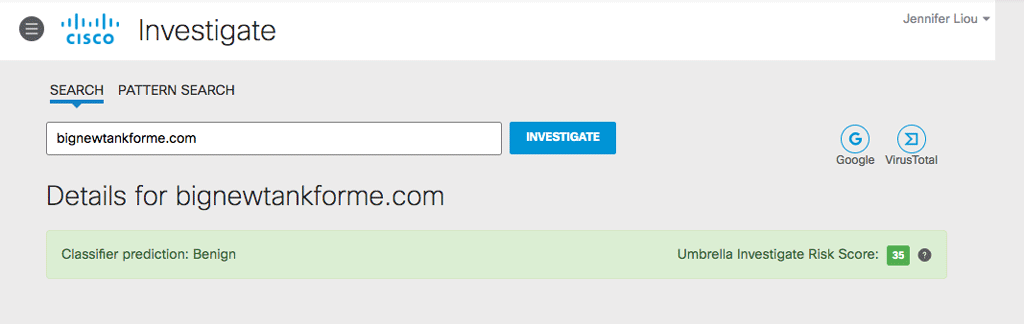
For example, upon first glance, this domain appears to be benign:
The domain currently has no security categories tagged to it (as of the publishing date of this blog).
However, Incident Responders or Threat Hunters would find it interesting that the domain is shown to have a history:
It was tagged in Feb 2017 as a domain used by malware called Pony (above left). We are further able to see that the domain tag was removed (above center) two years later, in Feb 2019, followed by an A record change (above right) a few days later. Incident Responders and Security Analysts may or may decide not to permit traffic to this domain depending on the risk tolerance unique to their organizations, but having this additional context at their fingertips help these teams make better informed decisions.
Other concerning scenarios include BGP hijacking – monitoring for certain DNS record changes can help prevent or speed up detection and response when certain records change to unexpected values. Also, domain convictions can vary in terms of speed to convict; even the best human analyst cannot convict with consistently high accuracy at nearly the same scale as a machine algorithm can.
By capturing up to four years of historical data, Investigate’s pDNS is much more than a traditional passive DNS database. By leveraging Investigate’s rich domain conviction historical data, you can uncover even more salient security events impacting your business, faster.
Learn more
Interested in checking out our Passive DNS capability? Contact us today for a demo or free trial for Cisco Umbrella Investigate.
If you are currently an Investigate customer, you already have access to our enhanced Passive DNS today. You will get up to 16x more pDNS historical data with no required action. Cisco Threat Response users who have an Investigate API license will be able to view pDNS data directly in the Threat Response dashboard.