Threats, threats and more threats! Cybercriminals won’t stop. Attackers relentlessly repurpose existing forms of malware delivery to find loopholes that compromise your employees and your business.
Data is your best weapon in the fight against cybercrime. Access to correlated security data can derail attacker efforts by improving detection and investigation processes and speeding your time to remediation.
Introducing Cisco Cloud Security App for Splunk Enterprise and Splunk Cloud
We’re excited to announce the Cisco Cloud Security App for Splunk Enterprise and Splunk Cloud. Drum roll please! What does this killer new app do? Simply put, it adds cloud security data and gives you the ability to correlate it with event data from Splunk to drive improved network visibility. The better question is — what can it do for you?
If you’re looking for better visibility into internet activity across all users and their devices, this app will be your new best friend.
With the new app you gain faster threat detection and greater context for investigations and mitigation response. What does it include? The app combines Cisco Umbrella DNS-layer security, secure web gateway, firewall, and cloud access security broker (CASB) technology, as well as threat intelligence from Investigate with Splunk in one streamlined workflow. This means you get better internet threat detection, tighter cloud infrastructure security, and advanced contextual intelligence.
A single dashboard for investigation
Who likes jumping from system to system and screen to screen? Not me! It’s not easy to be a security operations center (SOC) analyst or threat hunter these days. It can be very challenging to correlate information and ensure you’re not missing something critical. It’s harder and harder to stay on top of all the tools, alerts, and systems at your disposal. The need for a single, correlated source of information that helps analysts and threat hunting teams quickly uncover threats, identify risk, and prioritize incident response to speed remediation efforts is large.
Simplicity for the win
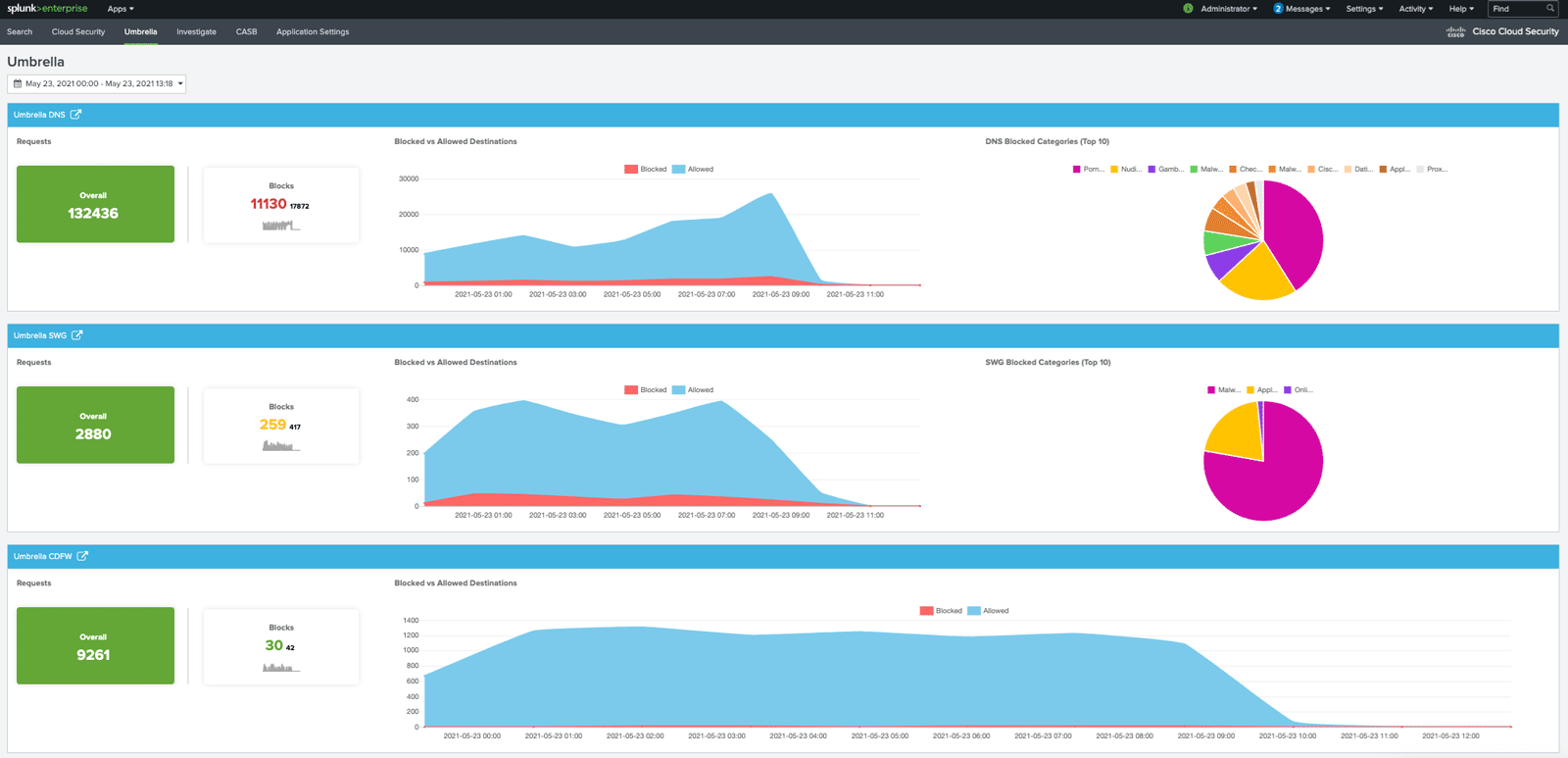
The Cisco Cloud Security App for Splunk was built with simplicity in mind. The goal is to help simplify threat analysis for SOC analysts, security admins, network admins, and threat hunters. We’ve created a single place to go to understand their Umbrella secure internet gateway traffic, so security staff can quickly identify and mitigate risks, improve investigation, and reduce remediation time. By integrating the Umbrella S3 logs and cloud security APIs into Splunk, users gain access to critical information from multiple cloud security systems in a single dashboard.
Simplify threat analysis with the Cisco Cloud Security App for Splunk and gain:
- An easy way to correlate data across systems
- Prioritization across disparate systems for remediation tasks
- Context for investigations
- Ability to manage incident response with ease
If you’re looking for better visibility into internet activity across all users and their devices, this app will be your new best friend. Administrators can easily see their Umbrella system status and compare it to a previous point in time to identify risks, trends, and anomalies for better investigation and faster remediation. Analysts can access users’ DNS, firewall, and secure web gateway activity in Splunk – to quickly see trends, as well as the number of domains allowed and blocked, compromised users, and devices. It also includes CASB data, Cloudlock incidents, and Umbrella Investigate threat information together with Splunk data.
Yes, attackers will continue to advance with new techniques and tactics. But we will continue to innovate and win with investigational insights.
Learn more today in the Cisco Cloud Security App for Splunk datasheet.

