Cisco Umbrella is widely recognized as one of the strongest products on the market for a secure and fast connection to the internet. And we are always looking for ways to deepen visibility and control for our customers. This is why we are teaming up with BlueCat, a leading provider of DNS, DHCP, and IPAM (DDI) management solutions.
Studies show that 91% of malware uses DNS to establish command and control callbacks, navigate through network pathways, and exfiltrate data. Cisco Umbrella fills this traditional gap in network security by blocking the outbound requests made to the malicious domains. When Umbrella customers point their network traffic to our resolvers they get visibility into the egress (external) IP address of their network. By leveraging capabilities such as the Umbrella roaming client, Umbrella virtual appliance or AnyConnect integration, customers can get additional attribution such as Microsoft Entra ID user names, internal IP addresses and hostname of computers.
With the BlueCat DNS Edge integration, customers get greater visibility into the attribution of the external DNS query (ie. the source IP), as well as additional control with the use cases outlined below. This integration expands the use cases for DNS security into investigations of internal network traffic, restricting lateral movement, and decreasing forensic response times. The integration enables customers to get full visibility and protection for DNS traffic leaving your environment for users on and off network.
How It Works
DNS Edge deploys as a virtual machine at the “first hop” of any DNS query. This gives DNS Edge the ability to tie every request on the network to a specific device without the need for an agent. With the integration, BlueCat Edge sends additional attribution information (ie. internal client IP) for each external DNS query to Umbrella. This allows viewing of device-level data directly in Cisco Umbrella, providing more granular information into the source of network threats.
Expand network visibility and control with the Cisco Umbrella and BlueCat integration
Use Cases
Investigate internal, “east-west” traffic: BlueCat’s “first hop” position on the network provides visibility into internal, “east-west” traffic – that’s 60% of all network queries – which mostly go unmonitored today. You can investigate internal traffic within DNS Edge, or send it to a SIEM and correlate it with other threat indicators. Using DNS Edge to apply security policies to this internal traffic means that security teams can contain lateral movement associated with advanced persistent threats and malicious insiders.

This screenshot shows how internal traffic appears in DNS Edge. Searching by source IP, you can see all internal and external domains queried by that device, and refine the search further by subdomains or any other factor you choose. In this example, you can see how a query to a known bad domain then results in lateral movement to other internal resources. This expands your visibility beyond the external domain that is shown in Umbrella.
Investigate lateral movement from IoT devices without agents: The threats to Internet of Things (IoT) devices are well known but difficult to properly control at an enterprise level. Since many IoT devices lack the capacity for security agents or any external software, blocking DNS queries as they leave the device is both a more elegant and more operationally feasible way to control a fleet of sensors at the enterprise level.

Here’s an example of how a rogue IoT device would look in DNS Edge. This is a security camera which should only ever be hitting a single internal domain. When it unexpectedly connects to an external domain (in this case, easyridegolfcars.com), this is the first indicator of a compromise. Looking at the subsequent queries, you can see both lateral movement to internal domains as well as potential data exfiltration attempts to the same external site.
Improve forensic response time: With all of this new data at their disposal, security teams are cutting their response time significantly – from days to minutes. Forensic investigators and threat hunters no longer have to compile DNS logs from recursive servers to find a source device – the data is available right in Cisco Umbrella or can be exported directly to a SIEM for further analysis. The rich context available from internal DNS data adds a new dimension to that analysis as well, uncovering additional connections to malicious activity.
Improve network performance: Device-level DNS data is a critical source of intelligence on how networks are performing. With visibility into the source, type, and result of every DNS query across the network, operators can quickly spot DNS misconfigurations, architectural shortcomings, misbehaving clients, and a host of other issues that may be impacting network performance and client reliability.
Getting Started
With a few simple steps, you can connect Cisco Umbrella to DNS Edge and start applying security policies. This integration leverages the network device API integration available in Umbrella. This allows for additional attribution information to be sent from the BlueCat Edge device to Umbrella. This allows the investigating user to see the internal IP of the requesting client instead of just the egress IP that Umbrella would see in a traditional network deployment.
Follow the steps below to take advantage of this integration.
1. Start off by creating an API key in Cisco Umbrella – you’ll want to choose the “Umbrella Network Devices” option.
2. Add that API key into DNS Edge. To do this, go to the Cisco Umbrella Integration tab on the main menu of DNS Edge. Paste in the API key and the secret.
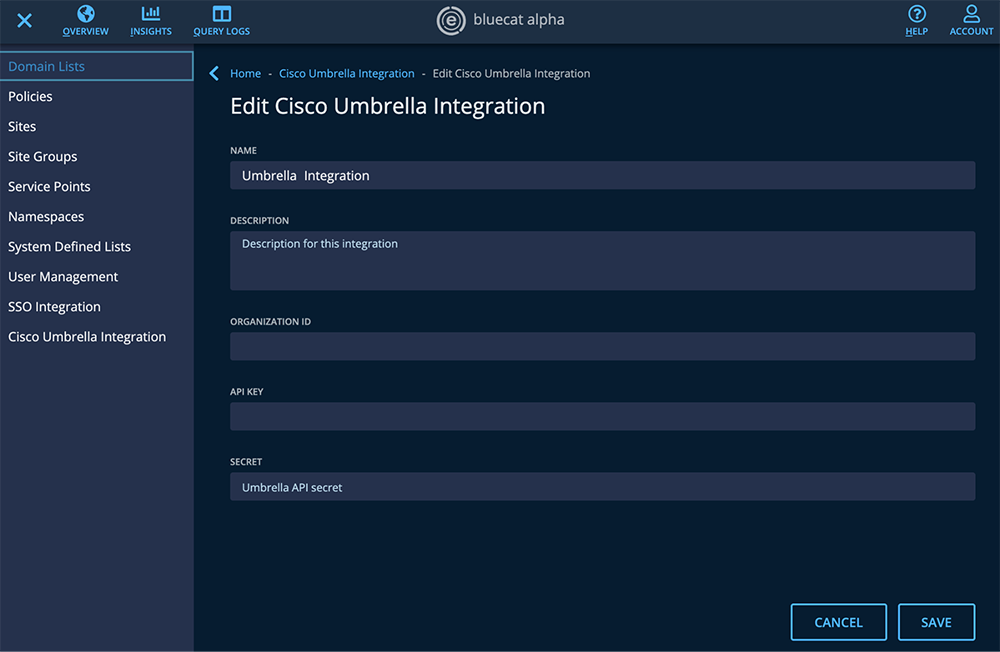
Once the API key is inserted, DNS Edge will appear as a network device within Cisco Umbrella. Initially, it will appear as “offline”, but will automatically switch to “active” once the data starts flowing.

3. Create a policy within Cisco Umbrella to handle external-facing traffic which comes from the DNS Edge service point (network device), just as you would do for any other network device.

When looking at the DNS queries in Umbrella you will now see additional attribution. For example, in the screenshot below we can see which Edge device the query came from, alongside the internal IP of who made that request.

Want to learn more?
Cisco and BlueCat recently presented this new integration at a Tech Field Day event. You can check out the session recording, as well as the Cisco Umbrella BlueCat integration data sheet to learn more.
This new integration with BlueCat adds one of the largest providers of DDI services to Umbrella’s integration arsenal, expanding on our existing integration with EfficientIP. If you’re heading to Cisco Live Barcelona next month be sure to stop by the BlueCat booth or La Taberna where Cisco Umbrella will be serving coffee and beer throughout the day. We would love to see you at the show!
