
At BSidesNYC we wanted to offer a more inclusive environment for our attendees so we decided a good first step was to set a goal that 50% of our speakers be women.
We didn’t make it – but we tried. In this post, I hope to share with you what we did so that maybe your security conference can make it to 50%.
Just a couple things to note:
- We didn’t ask anyone their gender and thus all charts that compare counts of men vs women may be inaccurate.
- There are many ways to set inclusion goals at conferences, my aim here is not to debate the goal itself, but share what we learned pursuing a goal we felt was right for us.
- Finally, the opinions expressed here are my own, and don’t necessarily reflect that of my employer, conference organizers, or attendees.
A Warm Welcome
Our first goal was to offer up a warm welcome to anyone looking at our website. We did this by enlisting supporters, partnering with organizations that shared our views, and creating a welcoming environment.
Enlist Amazing Supporters
Conferences boil down to the people who attend them and the experiences those attendees have. Before our website had sponsors, speakers, or an agenda, we had a freaking awesome wall of brilliant minds in security – most of which were women. We asked accomplished people within our social circles to sign up as ‘Supporters’ – allowing us to showcase them on our site to draw in a more inclusive crowd.

This was intentionally meant to send a clear message to attendees and potential speakers: women are welcome, smart people are here.
Supporting Organizations as Partners
In the same vein, we also reached out to groups that support women in technology, such as Women’s Society of Cyberjutsu, Women in Security and Privacy, and the Executive Women’s Forum, offering them free promotion for doing nothing other than letting us show support for them at our conference. Start early though, at least one of these partnerships took 4 months of persistent, mostly unanswered emails.

Anti-Harassment Policy
I’ll never forget the quick request-response I got when I asked one person to be a supporter:
Me: Would you want to be a Supporter for BSidesNYC, I think you would really help in encouraging more women to attend.
Person: Do you have an anti-harassment policy?
I’m not sure if this soon-to-be-supporter meant to imply that they would only join if we had such a policy, but that’s exactly how I took it. This question was an early indicator that we had enlisted a great supporter – our Anti-Harassment/Code of Conduct Policy not only showed that we were creating a safe place for our attendees, it also gave us clear instruction later on when we needed to handle reports of sexual harassment. You absolutely need this.
Soliciting CFP Submissions
A goal of 50% women speakers is deceptively difficult. No self-respecting conference in security would grant someone a technical speaking slot based on their gender or anything other than their knowledge. This means that in order to achieve the goal, not only do you have to spend time reaching out to women, you have to choose those who’ve done amazing research that will likely be accepted by the Call for Papers (CFP) board.
To make things even more of a challenge, if you’re only aware of a particular woman’s incredible research through reading their papers or watching videos of their talks, and not by knowing them, you’ll essentially be forced to cold-call these people and ask them to submit.
So that’s what we did – we reached out to over 40 women in the months before BSidesNYC, via Slack, Twitter, Email and LinkedIn.

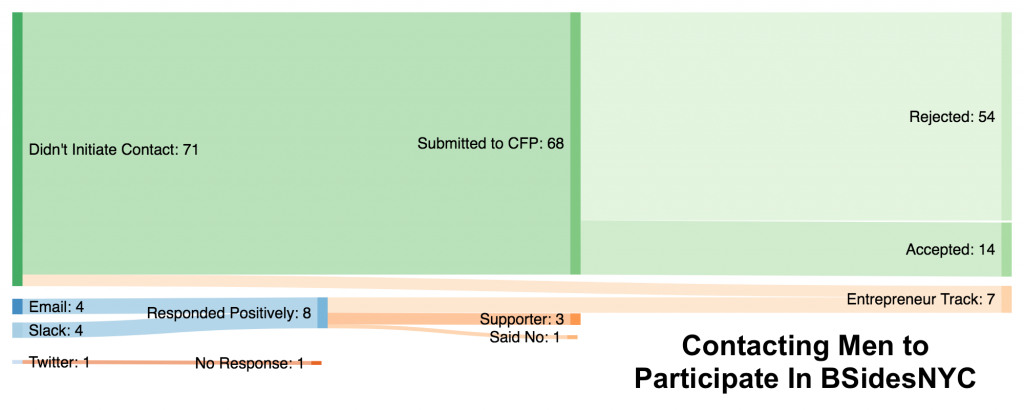
Just to contrast, this is effort we spent soliciting speakers who were men:
Finding Women
Anyone who tells you they can’t find women speakers in security hasn’t tried looking. Our industry may be grossly unbalanced, but that doesn’t mean we don’t have many extremely talented women.
Here’s a few places to find names to search, figure out if they’re in security, and if they’ve done research your audience might like:
- Search through talks given at all the major prior conferences
- List of Women Speakers in Tech
- Women and Tech
- Follow Friday Tweets like these, they’re really good
#FF #womenintech awesome group! @s0ciabl3ng@hexwaxwing @ivydigitalstorm @emilymaxima @apiratemoo @Dinah_Davis @s3scand0r @cybertri_x @InfoSecSherpa @RachelTobac @asbluecio @_Joyous_ More to come next week. #cybersecurity
— Marcelle (@marcelle_fsg) January 12, 2018
The Failed Pitch
Cold-calling is not easy. Initially my pitch to women who I didn’t know was:
Hi! I have a goal to reach 50% women speakers at BSidesNYC, would you consider submitting to the CFP?

Keep in mind I didn’t blast this out to just anyone – I researched loads of women and only contacted the ones I thought previously presented on topics our CFP board would accept. My objective with the pitch was to be succinct while perhaps appealing to their willingness to get behind a good goal.
Well, it turns out, it is more complicated than that.
Don’t Promote the Goal, Just Pursue It
Part of the reason we failed to reach our goal was that it took me too long to realize that if you want 50% women speakers, don’t tell anyone about it. Instead relentlessly pursue the goal without mentioning it. That means no public tweets, no DMs, no emails, no “50% women speakers” banners, no lapel pins, nothing.
Perhaps unsurprisingly, women (like everyone else) want to be recognized by their technical ability, and not because of their gender. By leading with “I have a goal to reach 50% women speakers”, I was essentially saying “I’m contacting you only because of your gender”.

These women had no clue I already vetted them and I was only reaching out because I admired their work. I was too worried about overcoming the challenge of cold-calling that I didn’t realize I was tragically sabotaging myself in the first couple words.
Looking back on this DM, I remember interpreting the response as “You are being very to the point” rather then, “You are only asking me because I’m a woman”.
Don’t let the same thing happen to you. Take the time to craft a genuine, personalized and meaningful request to each person you asked. No it’s not scalable. Here’s the type of approach I switched to later on, that yielded a much better result:
Hi! I absolutely loved your work on XYZ, would you consider submitting to the BSidesNYC CFP?

That’s so much better. Although it is hard to say if this new approach was the only deciding factor between these two examples, this person did present at the conference.
Extend Your CFP Window

We increased the amount of time the CFP was open so that we had more time to raise awareness about the conference. It also gave us a little more time to reach out to potential speakers. The data doesn’t show this had a profound impact on submissions, but I have to believe the extra time helped at least a little.
Traditional Problems Still Apply
Just because you’ve set this ambitious goal of 50% women speakers, doesn’t exclude the fact that travel can a be barrier, especially when you’re a smaller conference (BSidesNYC had about 630 attendees). Even though attendees and speakers came from all over the world, we had the most success soliciting speakers in the same geographic region as the conference.
The Internet is full of strange people, don’t expect everyone to believe you’re genuinely interested furthering inclusion in security.
I hate to break it to you, but people might not want to speak at your conference! Sorry!
An Unsettling Dose of Reality

The more women you reach out to, the more likely you’ll begin to feel how much of a problem sexual harassment really is. The one positive thing that came out of mentioning the goal was women began to explain a little more deeply why they wouldn’t submit:
It may not be surprising to the women of our industry, but the latter part of this response totally caught me off guard.
Stand Behind Your Goal
The exchange in the previous section was a prelude to some of the issues our industry is facing that you might not be expecting. Over the course of planning for the conference we received and handled anonymous reports of sexual harassment, warnings from women about specific people in the industry, and concerns from multiple speakers about individual attendees whose goal might be to threaten the safe space we created.
Good thing we had those awesome supporters, they were able to bring a much needed perspective to the mostly male BSidesNYC coordinators.
As you pursue your goal, be prepared to revoke tickets, dedicate ‘invisible protection’ for speakers, constantly remind everyone of your anti-harassment policy, issue firm warnings, and be willing to kick someone out of your conference in the spirit of creating a safe place for your attendees.
Making/Not Making the Goal


In the end, I underestimated how difficult this goal was, started too late, and needed to refine my pitch to women. By the time I figured this all out, the CFP submission period was over. Just by looking at the gender breakdown of the CFP submissions, I knew I didn’t have a chance of making it:
Another initiative I championed was the BSidesNYC Entrepreneur Track. Instead of completely ditching this goal, I decided to do whatever I could to still honor the intent of inclusion at our event. There was one important thing to note – since it isn’t a technical track, it isn’t subject to the CFP committee review. I still spent a lot of time researching, selectively choosing the speakers, and individually asking them to participate, but this time it was solely up to me to decide who got a speaking slot. You can see how this played out in the graph below.
You have no idea how happy I was during the brief moment that those red and blue lines met,
Cheater!
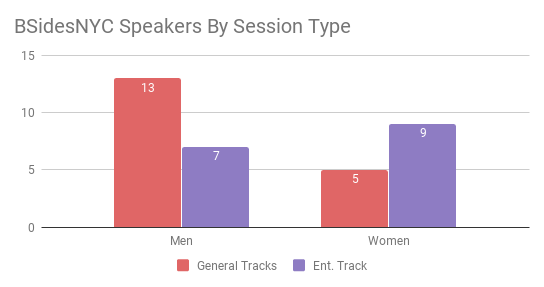
I have to admit, every time we talk about the goal, a part of me feels like we cheated. When the dust settled, 41% of our speakers were women, but this was mostly due to the Entrepreneur Track. If we only compared general tracks, we’d be at 38%. The further you dice it, you begin to see that our smaller size helps us since a single speaker has a bigger percentage impact compared to larger conferences.
Other Conferences

I began to grow curious how our conference compared to the larger ones. I took the likely flawed (again, no one was asked their gender) approach of looking at BlackHat and ShmooCon (CFP Metrics and Speakers), then comparing the two.
Looking at this data, perhaps a goal of 50% CFP responses from women might have been better. It’s interesting to see the larger conferences with relatively low percentages. I’d imagine they wouldn’t have the same challenges of getting a balanced CFP response.
Speaker Feedback

We sent a short survey to some of our speakers asking 4 questions, two of which being: “Do you Identify as a Woman?” and “Why did you submit?”. Eight responded “Yes or Partially” to “Do you identify as a Woman”. This is how those 8 replied to “Why did you submit” (participants could select multiple answers or fill in “other”):
It’s such a simple answer: If you want more women speakers at your conference, just create a place they want to speak at 🙂
Inclusion and Encouragement
This may be a rationalization, but the positive support from the community and countless people who have went out of their way to thank us for organizing such an inclusive conference leads me to believe that maybe all we needed to do was honor the intent of the goal to help make a tiny step towards progress.
A non-inclusive industry is one forcing itself to operate at a diminished capacity. It would be incredible to see other conference organizers setting a goal of 50% women speakers and doing it better than we did.
If you’re an organizer, on a review board, a potential speaker, or an attendee, I encourage you to contact the conference [early] and ask them to set inclusive goals. Organizers should also publish their CFP response and acceptance statistics so that as industry we can measure and learn.
In the meantime, we’ll work harder to create an awesome conference so that even more people will want to speak at it!
